
A pragmatic approach to disaster recovery
What will your business do in the face of a disaster? Does your business shave a disaster recovery plan? Is it up to date and has it been tested?
Read more…
What will your business do in the face of a disaster? Does your business shave a disaster recovery plan? Is it up to date and has it been tested?
Read more…
Digital transformation is driving the growth and adoption of Internet of Things (IoT) devices in the enterprise and the trend is accelerating at an unprecedented pace. IoT device growth is far outpacing the growth of more traditional computing devices such as laptops, desktops, servers, tablets and smartphones, so much so that the number of IoT devices in use is vastly greater than the number of people on the planet and growing by the second.
Read more…
In building your cyber security programme, you have likely focused on protecting your perimeter and keeping unknown threat actors from accessing your systems, networks and data. In doing so, have you ever considered what the people you trust are doing with their access to your systems, networks and data? You might have considered your top salesperson walking out of the door with their little black book, but the insider threat goes far beyond this.
Read more…
Alternatively, how did Barbara in Finance just download malware onto the network?
Read more…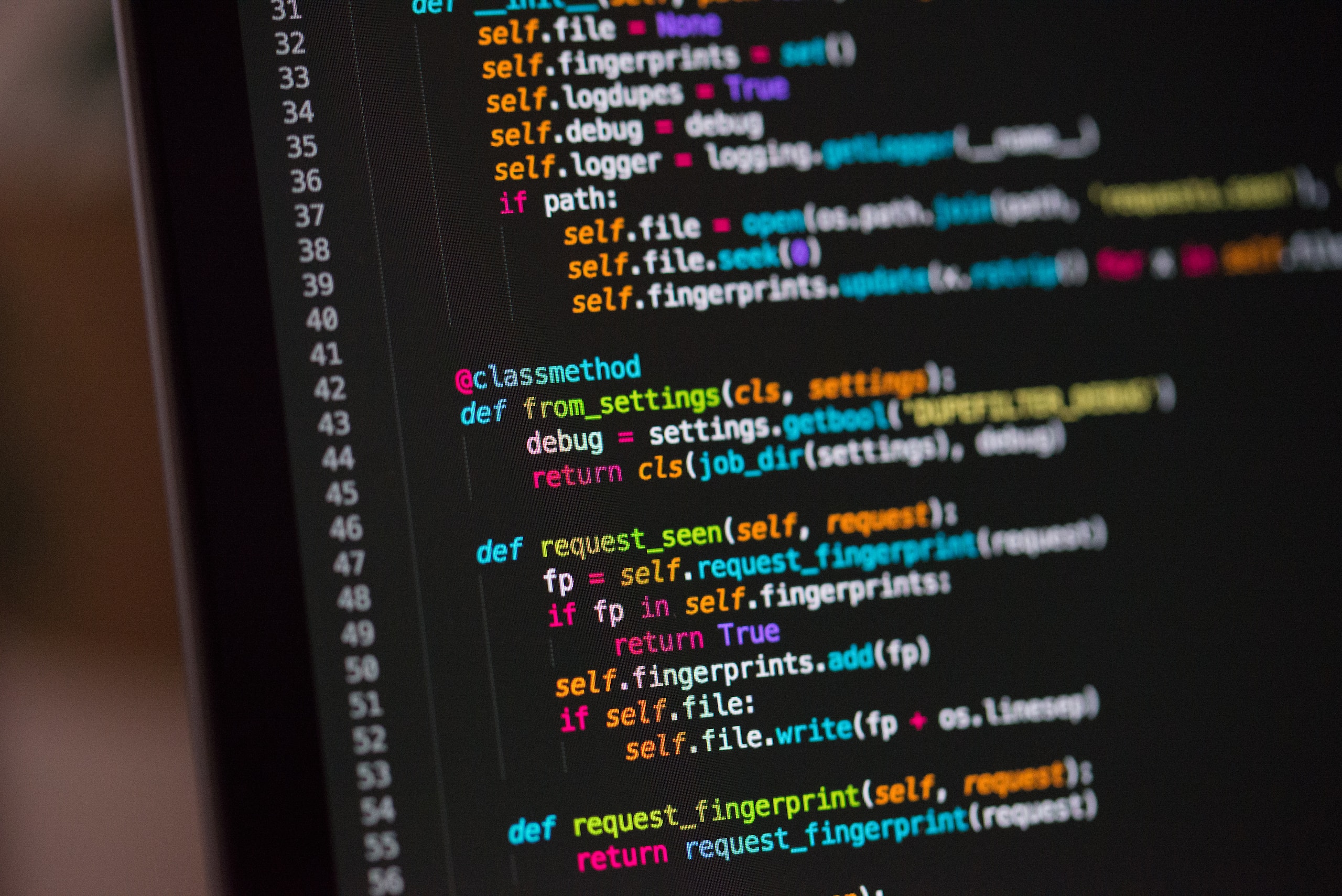
With this article, we hope to highlight good practices in software and application development. In short, what you should take into consideration to be able to develop secure applications and software, however and wherever they will be distributed. We will be predominantly talking about development practices, not DevOps, but we may revisit DevOps in future.
Read more…
The cyber kill chain describes the process a threat actor would typically take to execute a cyber attack, starting with the initial scouting and scoping and ending with the exfiltration or destruction of data or encryption for ransom.
Read more…
Zero Trust is simply a concept, a model which states that you really should not be trusting anyone or any device just because they reside on your network or within your perimeter.
Read more…
Last week, I was asked by Okta to speak at Okta Forum London about our implementation of their Single Sign-On and Multifactor Authentication products. We had considered Okta when we first implemented identity management, at the beginning of reed.co.uk’s journey into the cloud, however we didn’t sign with them until some time after, having watched their product’s development move at great speed.
Read more…
I’ve been building and hosting websites on and off for the last fifteen years, but, despite speaking French and German to degree level, it’s only recently that I’ve had to think about how to cater for non-English speakers.
Read more…
I’ve been using SSL certificates from Let’s Encrypt for a while now and though there’s no direct integration between certbot and nginx, it was all relatively straightforward to configure.
Read more…